WCS – The Internet Goes down Once and for All

Last updated - January 2015
Worst Case Scenario
The diversified 370+ (distributed around the world) 13 DNS Root name servers are hijacked and the master root zone file – which contains the database (IP addresses) of the Authoritative name servers of the Top Level Domains – is deleted permanently. To add up the adrenaline kick of destruction, let us also picture that the submarine cables are destroyed as well. Indeed, to complete the worst-case scenario, we still gotta blow up some internet exchange data centers around the world.
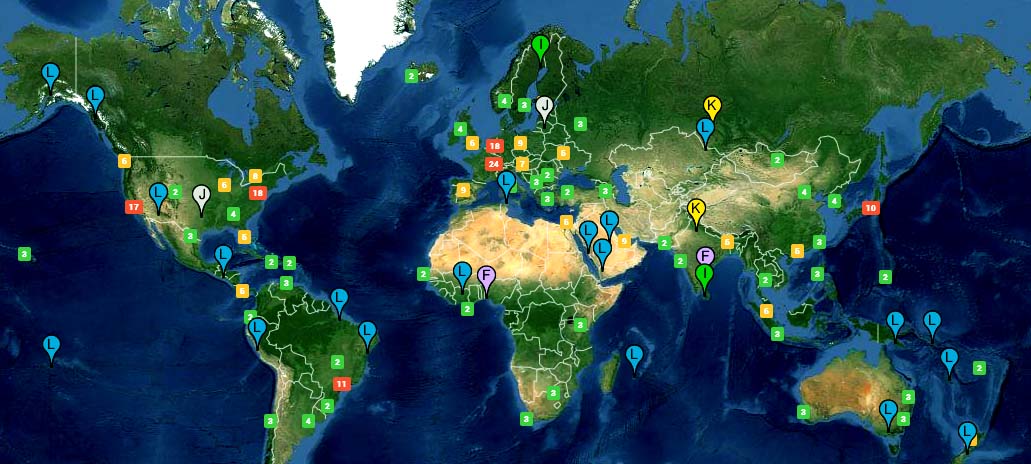
Interactive map – root-servers.org
So for the sake of the scenario let us assume that an evil hack army stages the attacks on the root servers by attaining the DNSSEC keycards, axes the undersea cables and screw up the authoritative name server of all the major hosts on the World Wide Web in a coordinated fashion. Let us also presume that it drops in a huge army of armed soldiers at every site, preventing any corrective measures or any repair attempts. In a few hours, the internet goes down completely and then starts a global pandemonium.
A little crash course
The comprehension of DNS and Root Servers would be helpful to go on with the WCS. It’s good to have a brief crash course on some basics to get along with this article and by hierarchy, let’s begin with the DNS and the DNS Root name servers.
DNS (Domain Name System) is a sophisticated internet translator that translates your www.geekswipe.net into 192.254.180.116 – more like a phonebook, that maps names to numbers.
DNS root name servers are the level one, name servers at the root of the hierarchy. A part of their database is called as the root zone. They hold the entire information/records about the top-level domain (.net .com .org and these) name servers (which stores another database that contains records and information about individual TLDs).
Now for example, let us consider the .net directory (directed from the root name server with the help of the information found from the root zone data). This .net name servers contains the information of all the .net Authoritative name servers (provided by the domain registrars).
Authoritative name servers are those that have the records, which have several records of www.geekswipe.net including the IP address 192.254.180.116.
Therefore, the flow of a DNS resolution starts with your browser entry, which uses a resolving name server like the OpenDNS or the one set up by your ISP. These resolving name servers go all the way to the root servers and then find the right TLD name server, from where they query the Authoritative name servers to find the IP address of the website you are looking for. This completes the DNS resolution in a blink of an eye.
Phew! Now back to the case
Now that you have an Idea how the internet works with DNS, you might understand what would happen if the root name servers are attacked. The root name servers would stop responding to the queries it receives, as their root zone file will be corrupted by the attacker. Then it will obviously disconnect the resolving server and the TLD name servers across the globe, and leave you empty handed without any webpages in your browser.
Is this the end?
While the world goes mad without the DNS, the internet will still be alive for a few who could connect by directly typing in the IP address of a website or who are smart enough to have their own name servers (Oh yeah! You gotta memorize the IP addresses for all the websites you wanna visit). The complete halt will be by axing the undersea cables, ripping off the servers from all the data centers, deleting the resolving server cache (If you can wait for a TTL expiry), multiple high altitude nuclear explosion to EMP the world (Well… That escalated quickly! Ignore it for this case anyway ;) ). Now, it’s definitely the end of the internet.
What happens next?
At this point, the world would’ve experienced the worst nightmare ever. People would’ve lost communication in a larger scale and probably would’ve penned their ‘vent off tweets’ in a paper. Governments start to collapse as their economy collapse over them with a heavy blow to their operation. While the Intranet survives on the other hand, the internal communication between local parties would sustain the attack.
Resurrection
Resurrecting the internet from the dead will be the first and foremost task. For a technical analysis, let us just assume that our government takes no action against those attackers and let them have all the 13 name servers with them for free (ahem! Not the zone files) and they in turn do nothing or just use them for some gaming stuffs. Let us also consider that the repairing the undersea cable is off the task list of the government. So what’s the new face of the internet?
It all could begin again from the level one, following our forerunner of the internet, the ARPANET. Using the same old protocols and principles people would be so desperate to star it from the bottom. Though conflicts are common to occur, no centralized medium will take part in the process, unless the organizations like the ICANN, IANA, W3C and similar internet groups join hands. New root servers will be deployed mostly, the surviving alternate root servers will come in to play for a while.
As the telecommunication sector suffers a huge blow to the operation, the necessity of communication outweighs the compulsion of a global order. This doubles the efforts to establish connections among the continents, before any one of the nuclear state blow up the whole world, initiating a nuclear war.
That 200KB file
So where does it all converge to? Major blackout will be due to the DNS root name server attack, in which the root zone file would be destroyed by the attackers. The zone file consists of all the information (IP addresses) of the top-level domains’ authoritative servers across the world. The size of the file is 200KB. It is okay to consider that this zone file is the backbone of the internet, as DNS would cease to exist (mostly) without this zone file.
Overview
As told earlier, unless otherwise the hacker force unites with a huge army and billion dollar ships and equipment, the internet is very safe and it will not end easily. And to add an extra layer of security, the ICANN (an organization that take cares of the root zone file along with VeriSign and other third parties) have implemented the DNSSEC, which is a standard that secures a certain DNS information, by digitally signing the DNS data and ensuring the data integrity throughout the transit. This provides an end-to-end authenticity with the help of digital signatures. While these systems can also be attacked, the Zone Signing Key (ZSK) is often changed to prevent any attacks, and these key are generated by another set of private authentication keys, called as Key Signing Key (KSK). Unlike the media hypes about the recovery key shareholders, they don’t actually safeguard the internet or can reboot the internet in case of a catastrophe, unless it is a direct attack on the DNS root zone files.

They actually have part of the master key to access a safe box that contains the keys to activate the new Zone Signing Key. At least five should be present to generate the new Zone Signing Key with their Key Signing Key. The infrastructures for those key generations are located on either coasts of the US, in a secure ICANN building surrounded with guards, located in safety deposit boxes monitored by seismic sensors.
Therefore, it is virtually impossible to attain these zone keys, and it is too damn hard to bring down the name servers as the world wouldn’t be deserted and the IT people and organization who manages the DNS would barge into the doors for the rescue.
Talking about the action part of the scenario, it is plausible. The submarine cables are axed many times in the history by both humans and natural disasters and it is likely to disrupt the internet rather than killing it. Still, there are hordes of redundant units at different location that are capable of taking over the loads until the axed cables are fixed.
As we possess the mighty powers to host our own root servers, to defend against axing of submarine cables, handle DDoS attacks in larger scale and infrastructure to run more redundant systems, the internet is… well.. let’s call it safe ;)
Even if the internet goes down, we still have the power to resurrect it from the root… So go see your cats now :)
This post was first published on March 4, 2014.










Alternate roots are so vulnerable. Imagine yourself landing on a yahoo search when you type in google. Host files will do that trick in a local machine.
I see Tacos in that safe!
I guess this scenario will be less dramatic than portrayed. There is always a way out of it and those copies are readily available on the web. But, what the hell :D This would make a great Spielberg flick!
Still, It’d be fun to watch the world without the internet, at least for a minute… 3:)
Awesome!
Thanks ;)