Self Replicating Malware – The Moon Worm – Infects Linksys Routers

In 2003, a computer worm called Blaster, also known as lovesan, was programmed to start a SYN flood, creating a distributed denial-of-service attack (DDoS) against the http port of windowsupdate.com. One of the executable messages stated “Billy Gates why do you make this possible? Stop making money and fix your software”. Although the target of the worm is the co-founder of Microsoft, the damage on the company was minimal.
In 2013, CryptoLocker, a ransomware trojan horse, targeted computers running on Microsoft windows. It encrypted the files on user’s hard drive, prompting them to pay a ransom to the developer via bitcoins or direct payment, in order to receive the decryption key, justifying the term ransomware.
As creative as they get, a recent attack on Linksys routers by The Moon worm, scanned for IP addresses in ports 80 (http) and 8080 (web proxy and caching). The attack is a self-replicating program that compromises the Linksys routers and using them to scan for other vulnerable devices. This was done by exploiting an authentication bypass vulnerability.
Authentication Bypass
Generally, coding authentication for web application involves a simple username and password in login page, allowing them unrestricted access. Turns out, that is not necessarily the only way to get access, least, for hackers. It is assumed that the only way to get into the configuration page is by racing past login. But what if, accessing them is possible without having to log in? Which is by the way, bypassing authentication.
Some devices have a list of restricted URLs that prompts the user for login credentials to access them. However, what if, there were alternative URLs that pointed to the same page, which also happens not be in that list? That is another authentication bypass vulnerability.
The Moon worm attack
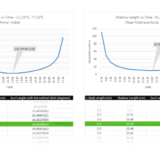
Back to the Moon worm, it begins the attack by requesting a /HNAP1/URL from devices behind the scanned IP addresses. The HNAP (Home Network Administration Protocol) allows configuring and managing the networking devices. So, the request to HNAP brings in the model of the router and version of the firmware. The device being vulnerable, allows the worm to send another request to a particular CGI (Common Gateway Interface) script which allows the execution of local commands.
The name of the CGI script that attacked the Linksys routers remains disclosed, having been known to have contained authentication bypass vulnerability. The worm sends random admin credentials but they are not checked by the script, which the Linksys was aware about. Following the CGI script request, the second request will launch a simple shell script that will request the actual worm, which is about 2MB in size.
Once the code is run, the router scans for other vulnerable victims around. Mission accomplished. It is then the dominoes start to fall. Upon scanning and infecting the victims, they in turn scan for more vulnerable devices around.
Origin
The Moon worm includes a list of 670 networks that also has basic HTML pages with images. The malware includes the logo inspired from the ‘Lunar Industries’ logo from the 2009 movie ‘Moon’. Hence the name. At this point, it is termed as a “worm”, as it appears that all it does is to spread.
Johannes B. Ullrich, of SANS Technology Institute, says that it could also be a “bot”, if it had a functional channel and control in it.
More updates on ‘The Moon’ worm can be found here and here.
This post was first published on February 17, 2014.